Simplify Your Procedures WITh Reliable Managed IT Provider
In today's busy service atmosphere, the function of technology in optimizing procedures has actually ended up being progressively important. Carrying out trustworthy handled IT services can be the key to improving your organization's procedures and boosting general efficiency. From improving your modern technology facilities to fortifying cybersecurity measures, the advantages of such services are significant. By making sure seamless everyday operations and positioning your organization to prosper in the ever-evolving digital landscape, handled IT services lead the means for sustainable development and success. The inquiry stays: just how can your organization take advantage of these solutions to acquire an one-upmanship and remain in advance of the curve?
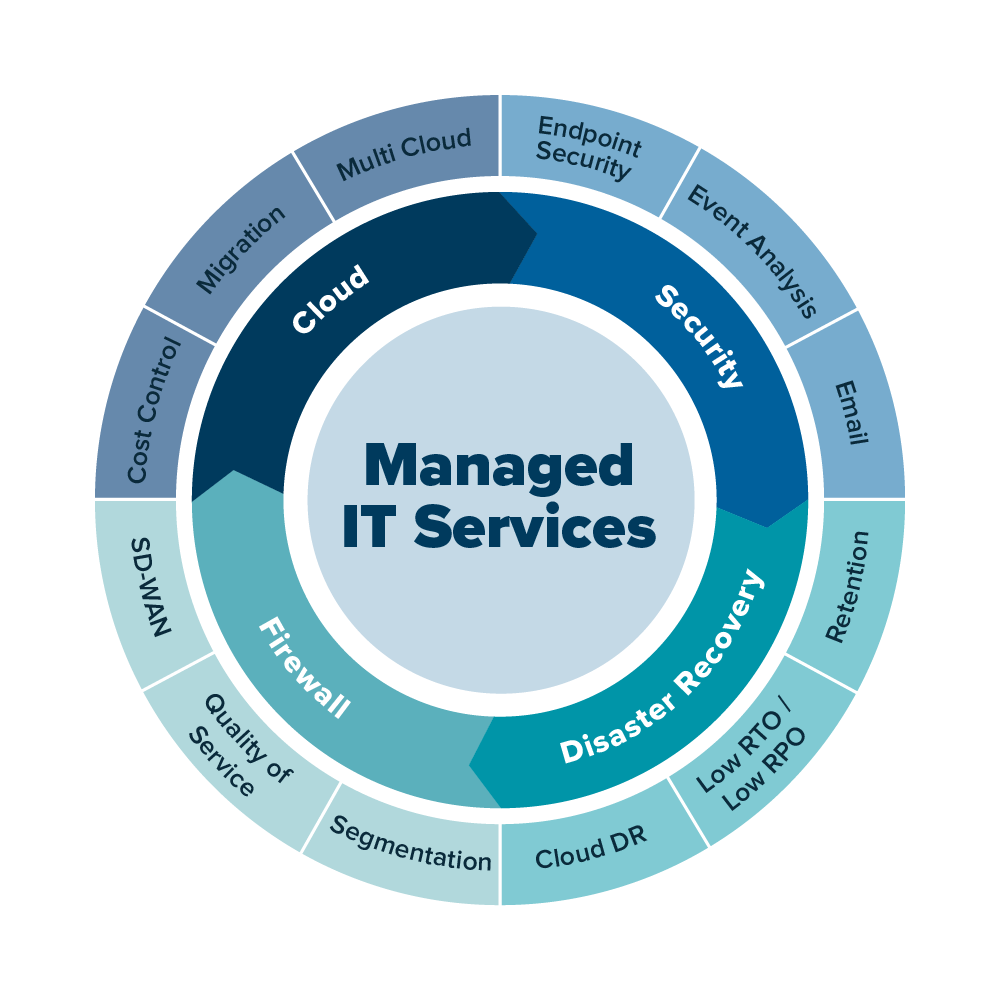
Enhancing Operational Effectiveness

Second of all, handled IT services provide accessibility to a group of proficient experts with know-how in various locations of info technology. This access to specialized expertise enables organizations to resolve complicated IT challenges properly and execute innovative remedies to enhance functional effectiveness.
Additionally, handled IT services can aid companies automate regular tasks, such as software updates and information backups, maximizing employees to concentrate on more critical campaigns. This automation not just conserves time however also minimizes the risk of human mistake, leading to even more trustworthy operations.
Improving Modern Technology Facilities
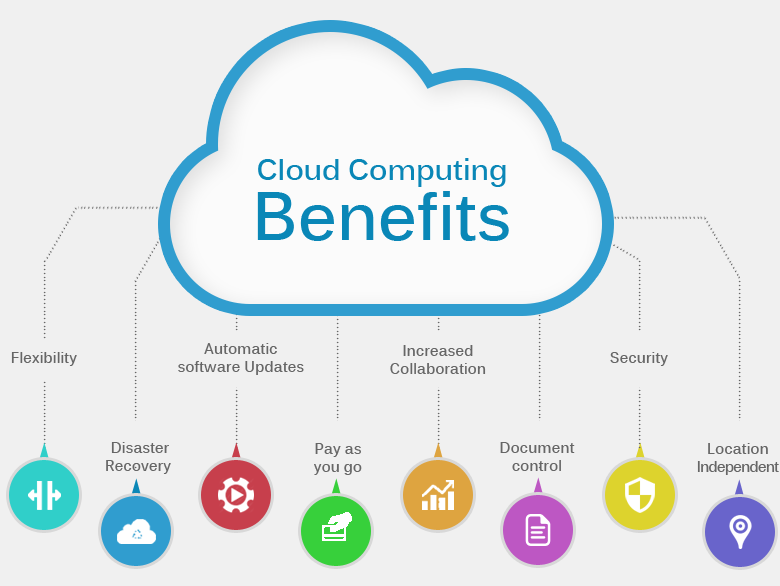
By maximizing their modern technology framework, companies can better boost their functional effectiveness with managed IT solutions. To boost innovation infrastructure, companies can utilize handled IT services that provide know-how in network administration, cybersecurity, cloud services, and IT support. By spending in boosting their innovation infrastructure with reputable managed IT solutions, organizations can optimize their electronic capabilities, increase performance, and remain competitive in today's technology-driven landscape.
Reinforcing Cybersecurity Procedures
Additionally, worker training on cybersecurity finest methods is crucial in producing a society of protection recognition within the company. Human mistake stays a considerable consider cyber breaches, making it vital to inform team on just how to identify and react to prospective risks efficiently. Additionally, developing incident response methods and conducting regular drills can aid ensure a swift and coordinated response in case of a security incident. By strengthening cybersecurity measures across all degrees of the company, companies can better secure their delicate information and keep the depend on of their stakeholders in an increasingly digitized globe.
Guaranteeing Smooth Day-to-Day Workflow
Keeping operational performance is critical for maintaining business success in today's affordable landscape. Ensuring seamless everyday procedures is important in achieving this performance. Managed IT services play a critical function in this facet by offering positive surveillance, quick problem resolution, and recurring support to keep service procedures running smoothly.
By partnering with a trusted managed IT services provider, services can streamline their daily procedures via efficient innovation administration - managed Get More Information it services inland empire. This includes routine maintenance of IT facilities, software program updates, and continuous technical support. Such positive procedures aid protect against unanticipated downtime and ensure that employees can concentrate on their jobs without disturbances
In addition, managed IT services offer tailored services to satisfy specific service requirements, whether it's cloud computer, cybersecurity, or data administration. This personalized method enhances operational efficiency by straightening IT sources with organization objectives and enhancing processes.
Flourishing in the Digital Landscape
In today's rapidly progressing organization environment, the capability to grow in the digital landscape hinges on properly leveraging managed IT services to maximize operational performance and adjust to technical developments. Handled IT solutions play a vital function in making it possible for organizations to browse the intricacies of the electronic landscape by providing company website proactive tracking, cybersecurity procedures, cloud remedies, and scalable infrastructure assistance.
Additionally, prospering in the electronic landscape calls for a tactical method to IT that lines up with service objectives and boosts total performance (co-managed IT services Lake Elsinore). Handled IT solutions supply customized remedies that satisfy details business demands, whether it be simplifying operations processes, enhancing information safety and security, or helping with remote work capabilities. By partnering with a reputable managed IT companies, companies can not just endure yet grow in the ever-evolving electronic landscape
Final Thought